On June 2nd , Japanese multinational conglomerate Fujifilm officially confirmed that they had suffered a ransomware attack that has disrupted their business operations.
Fujifilm disclosed that they suffered a cyberattack but would not confirm if the attack was caused by ransomware.
At approximately 10:0 AM EST on Tuesday, Fujifilm told employees to shut off their computers and all servers immediately. Furthermore, the network outage prevented access to email, the billing system, and a reporting system.
To alert their customers, Fujifilm also added notifications to their websites warning customers about the disruption to their business.
Fujifilm confirms about a ransomware attack
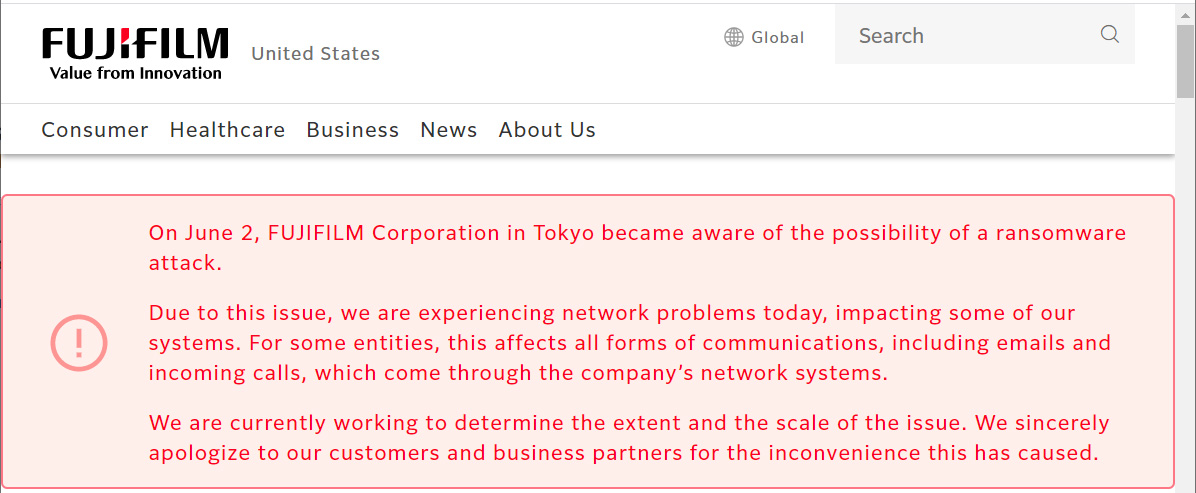
Fujifilm has released an updated statement that officially confirms that the attack was caused by ransomware deployed on the night of June 1st, 2021.
- We confirmed that the unauthorized access we recognized on the night of June 1, 2021 was ransomware.
- We have confirmed that the scope of impact is limited to specific networks in the country.
- Since the range has been identified, from today, we are proceeding with the operation of servers and personal computers that have been confirmed to be safe, and the networks that were blocked are also starting communication in sequence.
While it has not been disclosed what ransomware gang was behind the attack, it is believed to be the REvil ransomware operation.
Fujifilm had recently been infected by the Qbot trojan, which is currently partnering with the REvil ransomware operation to provide remote access to compromised networks.
Using the remote access provided by the trojan, the REvil ransomware gang will infiltrate a network and spread slowly to other devices while stealing unencrypted data.
Once they gain access to a Windows domain administrator account and have harvested any data of value, they deploy the ransomware throughout the system to encrypt devices.
If Fujifilm did not pay the ransom, we will know soon enough who was responsible, as the data will likely be released on a ransomware data leak site as a further method to leverage a ransom payment.