Chinese hackers are behind the most numbers of Zero day attacks in 2021.
By definition Zero-day vulnerabilities are security weaknesses in software products that are either unknown or have not been fixed at the time of discovery
Zero-day disclosures are of particular interest to hackers because they have a wider exploitation window until vendors address the flaws and clients start applying the updates.
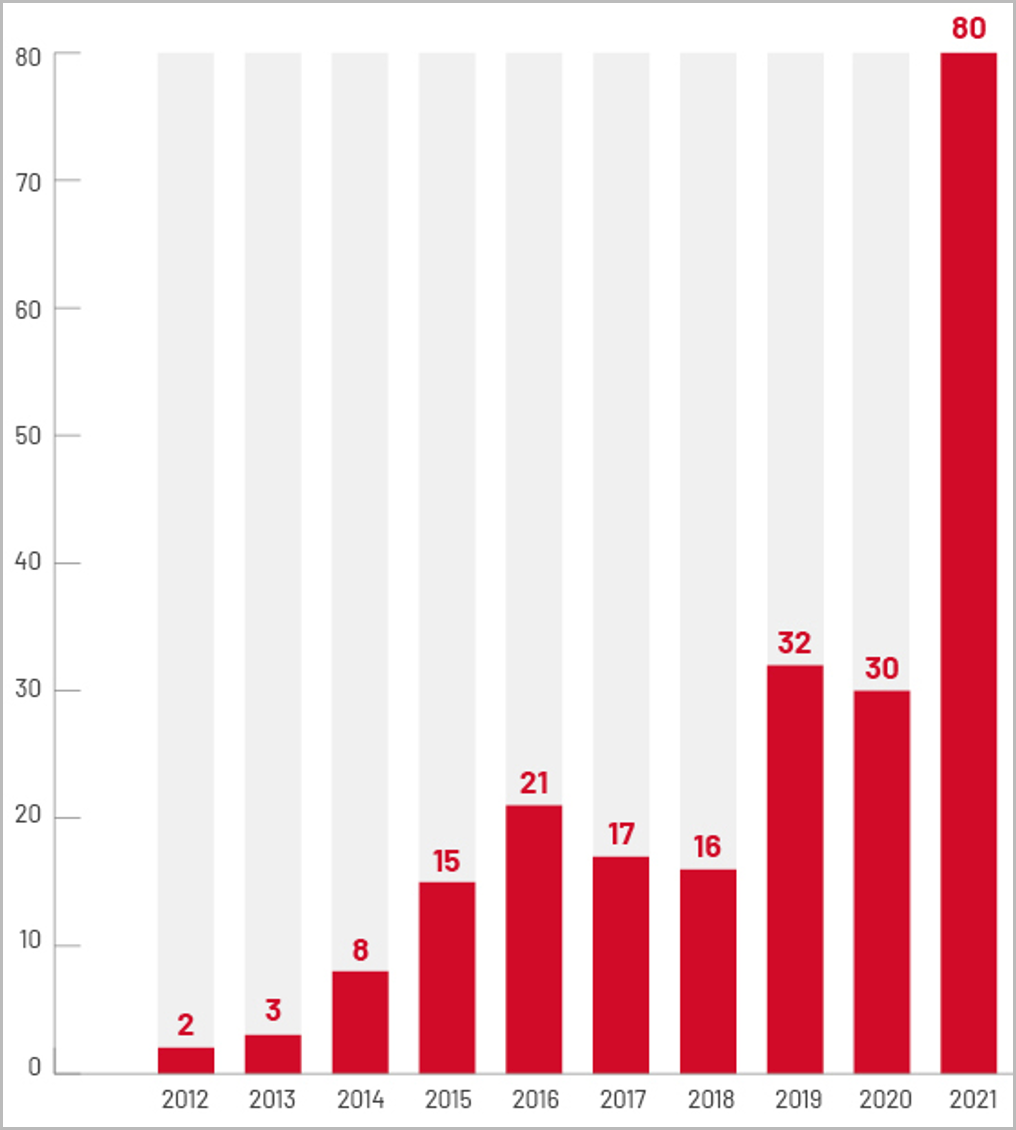
Typically, this window of opportunity lasts for at least a couple of days, and since not all admins apply security updates immediately, the number of vulnerable targets remains high for a while.
According to the Mandiant report last year there was 80 cases of a Zero day exploited in the wild. Most numbers of attacks are attributed to the state based actors.
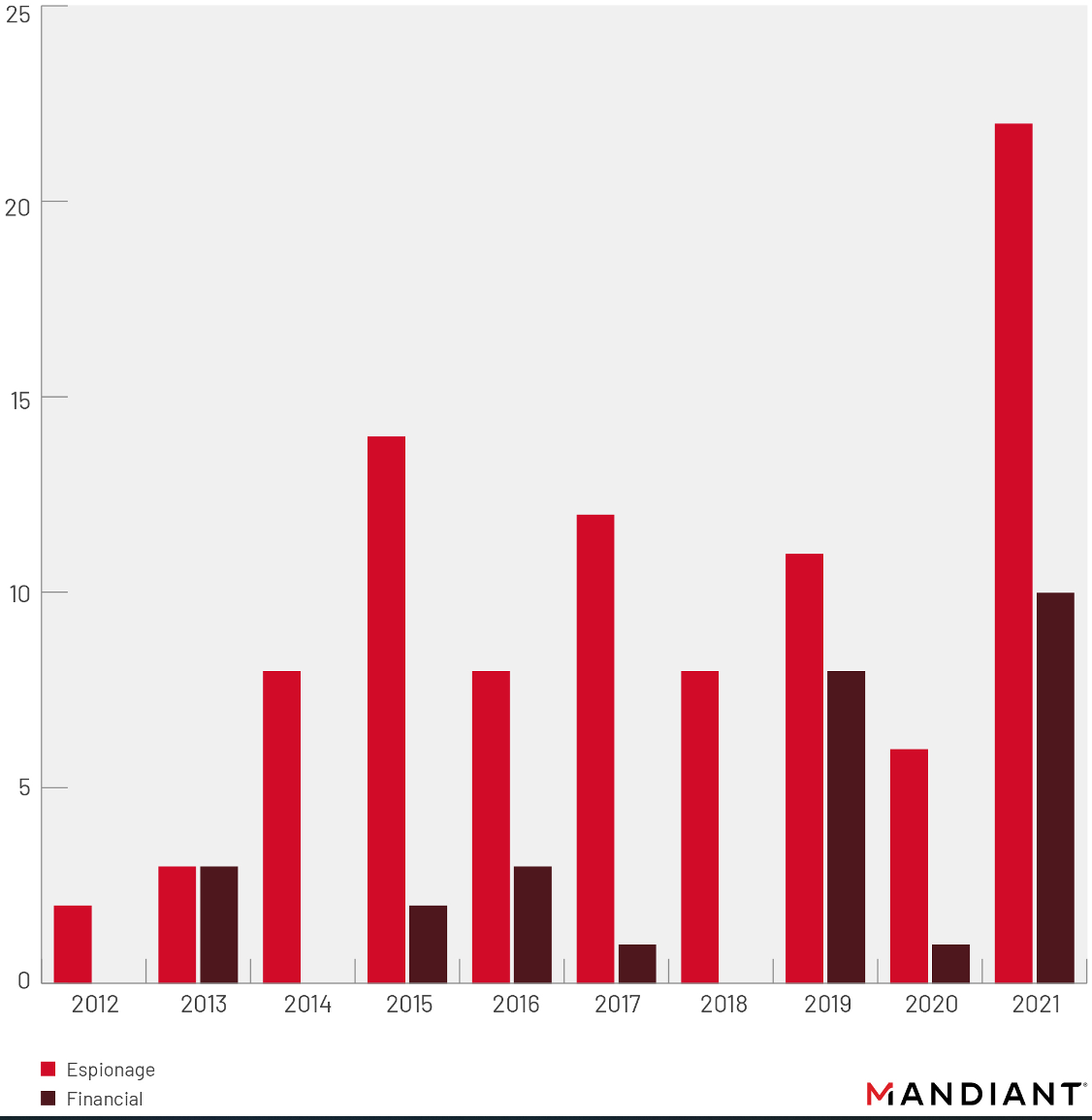
It was noted by Mandiant that one out of three malicious actors exploiting zero-day vulnerabilities was financially motivated, a statistic that continues a growing trend from previous years.
In terms of threat actors, China tops the list with eight zero-days used in cyberattacks in 2021, followed by Russia which used two, and North Korea with one.
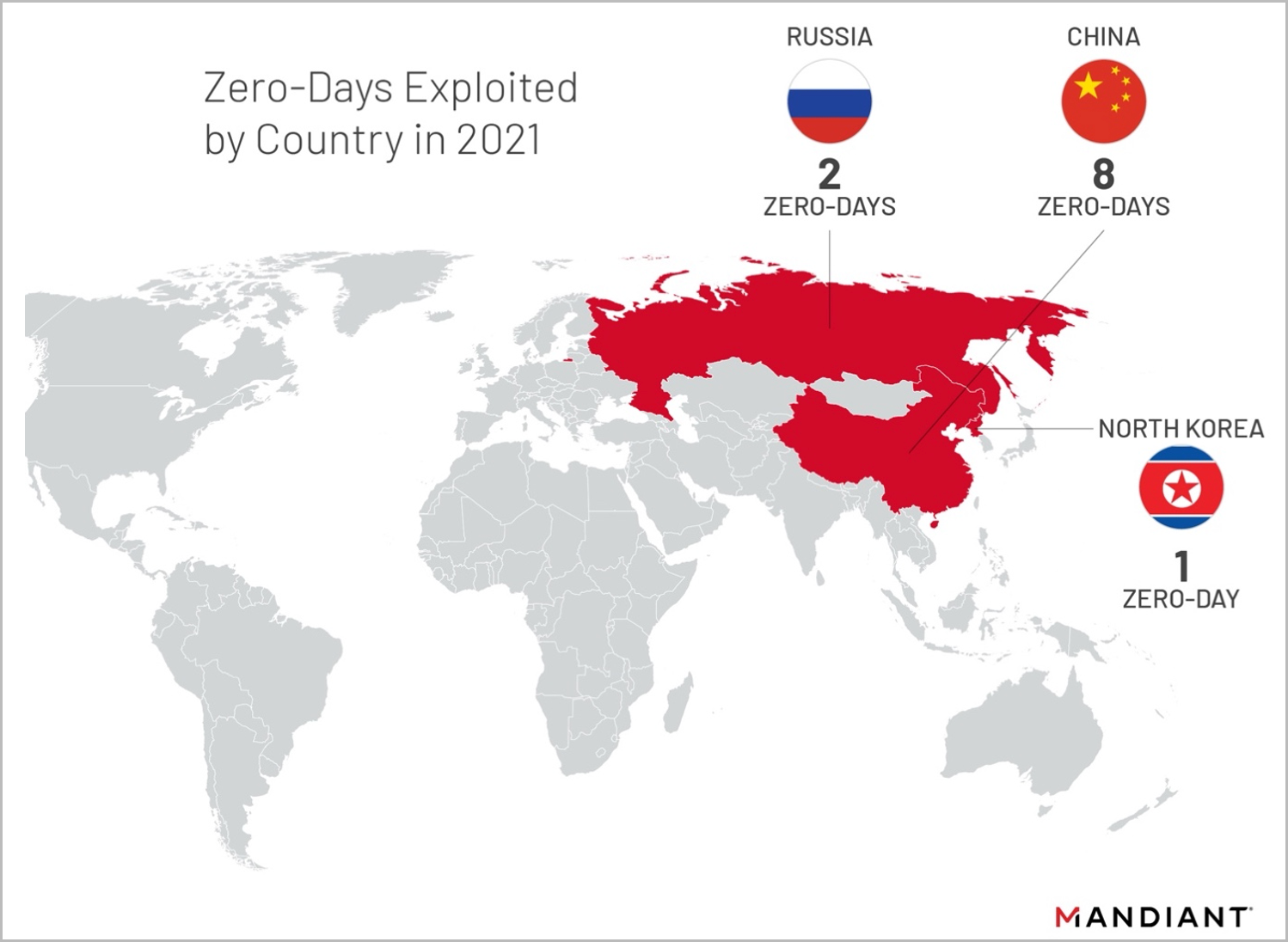
The most notable case was that of Hafnium, a Chinese state-sponsored hacking group that utilized four zero-day vulnerabilities on the Microsoft Exchange servers to access email communications of Western organizations.
Mandiant also recorded an uptick in ransomware operatives exploiting zero-day flaws to breach networks and deploy their file-encrypting payloads.
One prominent example of this activity was that of HelloKitty ransomware operators, who exploited a zero-day bug in SonicWall SMA 100 VPN appliances.
The most targeted vendors in 2021 zero-day attacks were Microsoft, Apple, and Google, accounting for over 75% of all attacks.
.png)
