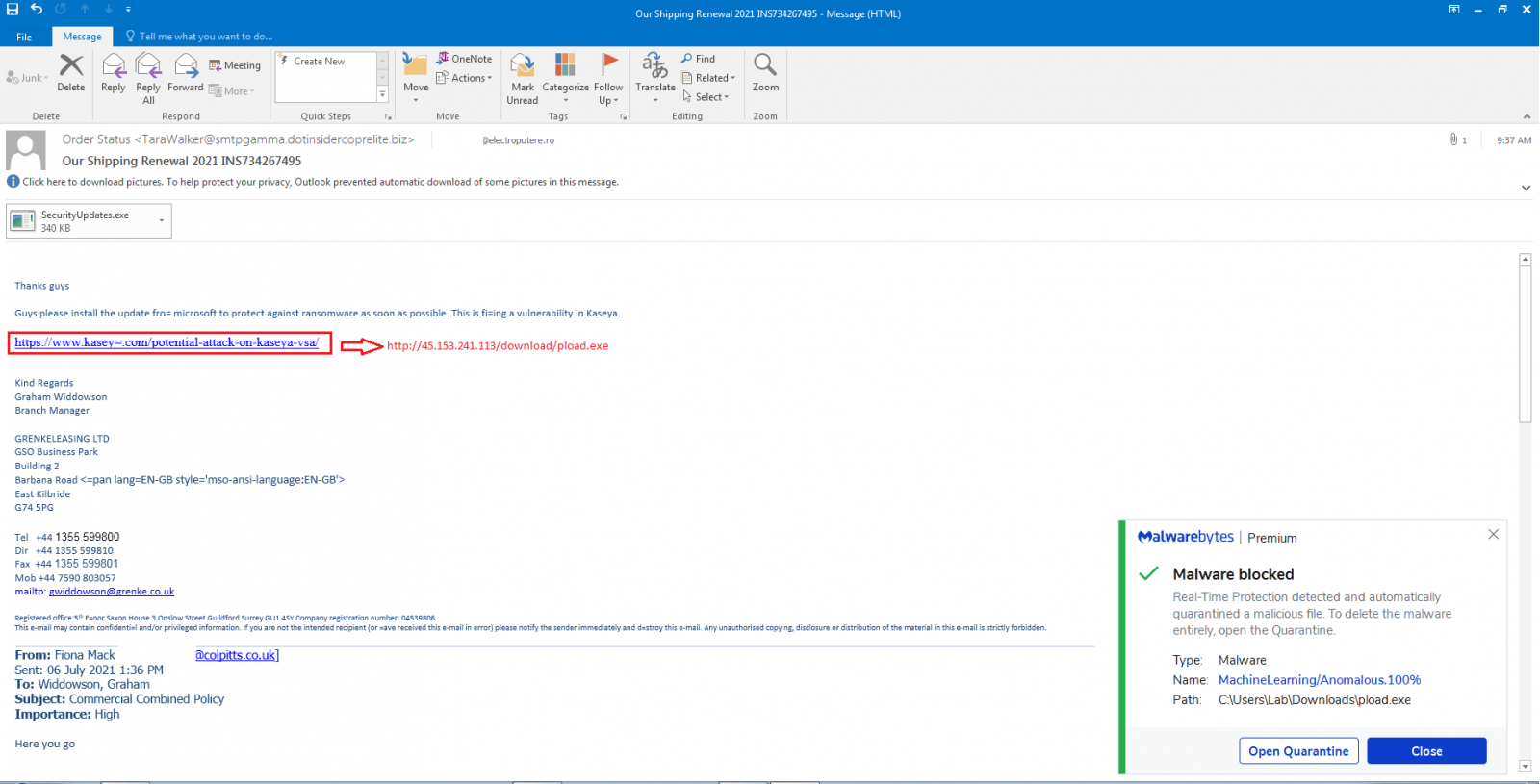
Kaseya customers are being targeted by the Threat actors using the SPAM mails. In the spam campaign attackers are pushing Cobalt Strike payloads disguised as Kaseya VSA security updates.
Cobalt Strike is a legitimate penetration testing tool and threat emulation software that’s also used by attackers for post-exploitation tasks and to deploy so-called beacons that allow them to gain remote access to compromised systems.
The end goal of such attacks is either that of harvesting and exfiltrating sensitive data or delivering second-stage malware payloads.
“Interestingly, 66 percent of all ransomware attacks this quarter involved red-teaming framework Cobalt Strike, suggesting that ransomware actors are increasingly relying on the tool as they abandon commodity trojans,” the Cisco Talos Incident Response (CTIR) team said in a September quarterly report.
Attack Indicator
The malspam campaign spotted by Malwarebytes Threat Intelligence researchers uses two different tactics to deploy the Cobalt Strike payloads.
Malicious emails sent as part of this malspam campaign come with a malicious attachment and an embedded link designed to look like a Microsoft patch for the Kaseya VSA zero-day exploited in the REvil ransomware attack.
“A malspam campaign is taking advantage of Kaseya VSA ransomware attack to drop CobaltStrike,” the Malwarebytes Threat Intelligence team said.
“It contains an attachment named ‘SecurityUpdates.exe’ as well as a link pretending to be security update from Microsoft to patch Kaseya vulnerability!”
The attackers gain persistent remote access to the targets systems once they run the malicious attachment or download and launch the fake Microsoft update on their devices.
Email IOC for this attack :[.]dotinsidercoprelite[.]biz
