Threat actors have stolen files from several official government agencies of Japan by hacking into Fujitsu’s software-as-a-service (SaaS) platform and gaining access to its systems.
The Japan-based tech giant temporarily disabled ProjectWEB enterprise after learning of the attack, which is known to have affected the Ministry of Land, Infrastructure, Transport, and Tourism; the Cabinet Secretariat; and the Narita Airport so far but may have had other victims, according to a post on analyst firm Recorded Future’s The Record.
ProjectWEB is a a cloud-based enterprise collaboration and file-sharing platform that Fujitsu has operated since the mid-2000s, and which a number of agencies within the Japan government currently use.
Fujitsu’s Cabinet Cyber Security Center (NISC), which is investigating the incident, said the breach was discovered on Monday and issued a release the following day with guidance to all government agencies to take countermeasures to see if they are using ProjectWEB.
If so, NISC advised agencies to investigate to see if they also were breached, according to a statement posted online Tuesday (PDF), and to report unauthorized access or data leaks.
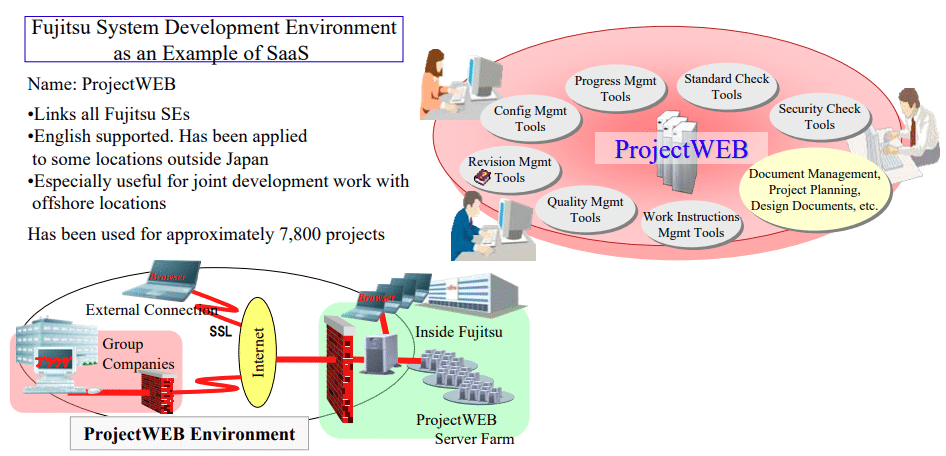
Platform Disabled
Fujitsu decided to suspend the operation of ProjectWEB on Tuesday following pressure from NISC, apologizing “for the great concern and inconvenience” the breach caused its customers.
“We will continue to work on investigating and analyzing the scope of impact and the causes of all projects that use [ProjectWEB] with the cooperation of our customers,” according to the statement (translated from Japanese). “We take this case very seriously and will continue to consult with the relevant authorities and make every effort to support the victims. that’s all Inquiries regarding this matter.”
Though Fujitsu did not disclose details about nor the scope of what was stolen, a report in the Japanese press claimed that attackers pilfered documents that contained more than 76,000 email addresses for employees and contractors for the Ministry of Land, Infrastructure, Transport, and Tourism.
Data on air traffic control also was nabbed from the Narita Airport, which serves Tokyo, according to a separate report by Japanese public broadcaster NHK. Authorities also have not disclosed any knowledge of who was behind the attacks nor what their motives may have been.
Government Targets
The attack is the second cyber incident the government of Japan has suffered in a month. In late April, threat actors leveraged two vulnerabilities in a popular file-sharing server from Japan-based Solito to breach corporate and government systems and steal sensitive data as part of a global hacking campaign that affected the Japan Prime Minister’s Cabinet Office. The incident was similar to the series of Accellion attacks that occurred earlier this year.
Indeed, government agencies and their affiliates around the world have suffered a rash of cyber attacks recently that caused varying degrees of disruption.
Effects of the ransomware attack earlier this month on Colonial Pipeline, a major U.S. oil supplier, are still being felt. About a week later, Ireland’s department of health was hit with two ransomware attacks—one successful, one failed—which interfered with health services and appointments and created tens of millions of dollars in damage.
The ProjectWEB incident also is not the first time Fujitsu had to disrupt a product due to a security incident. In 2019, the company halted sales of its popular Fujitsu Wireless Keyboard Set LX901 after a researcher discovered that it was vulnerable to keystroke injection attacks that could allow an adversary to take control of a victim’s system.
