At least on ransomware threat actor has started to leverage the recently discovered PetitPotam NTLM relay attack method to take over the Windows domain on various networks worldwide.
Behind the attacks appears to be a new ransomware gang called LockFile that was first seen in July, which shows some resemblance and references to other groups in the business was reported by bleeping computer.
LockFile attacks have been recorded mostly in the U.S. and Asia, its victims including organizations in the following sectors: financial services, manufacturing, engineering, legal, business services, travel, and tourism.
Security researchers at Symantec, a division of Broadcom, said that the actor’s initial access on the network is through Microsoft Exchange servers.
Symantec’s analysis of the attack did not reveal the exact method but they provided an IP address (209.14.0[.]234) that security researcher Kevin Beaumont saw in attacks that exploited the ProxyShell vulnerability since August 13. Beaumont also published a detailed blog post about multiple actors exploiting ProxyShell.
Next, the attacker takes over the organization’s domain controller by leveraging the new PetitPotam method, which forces authentication to a remote NTLM relay under LockFile’s control.
Discovered by security researcher Gilles Lionel in July, PetitPotam has a few variations that Microsoft kept trying to block. At this point, the official mitigations and updates do not completely block the PetitPotam attack vector.
LockFile threat actor seems to rely on publicly available code to exploit the original PetitPotam (tracked as CVE-2021-36942) variant.
Once the attackers successfully take over the domain controller, they effectively have control over the entire Windows domain and can run any command they wish.
Symantec says in a blog post today that the ransom note from LockFile ransomware is very similar to the one used by the LockBit ransomware group.
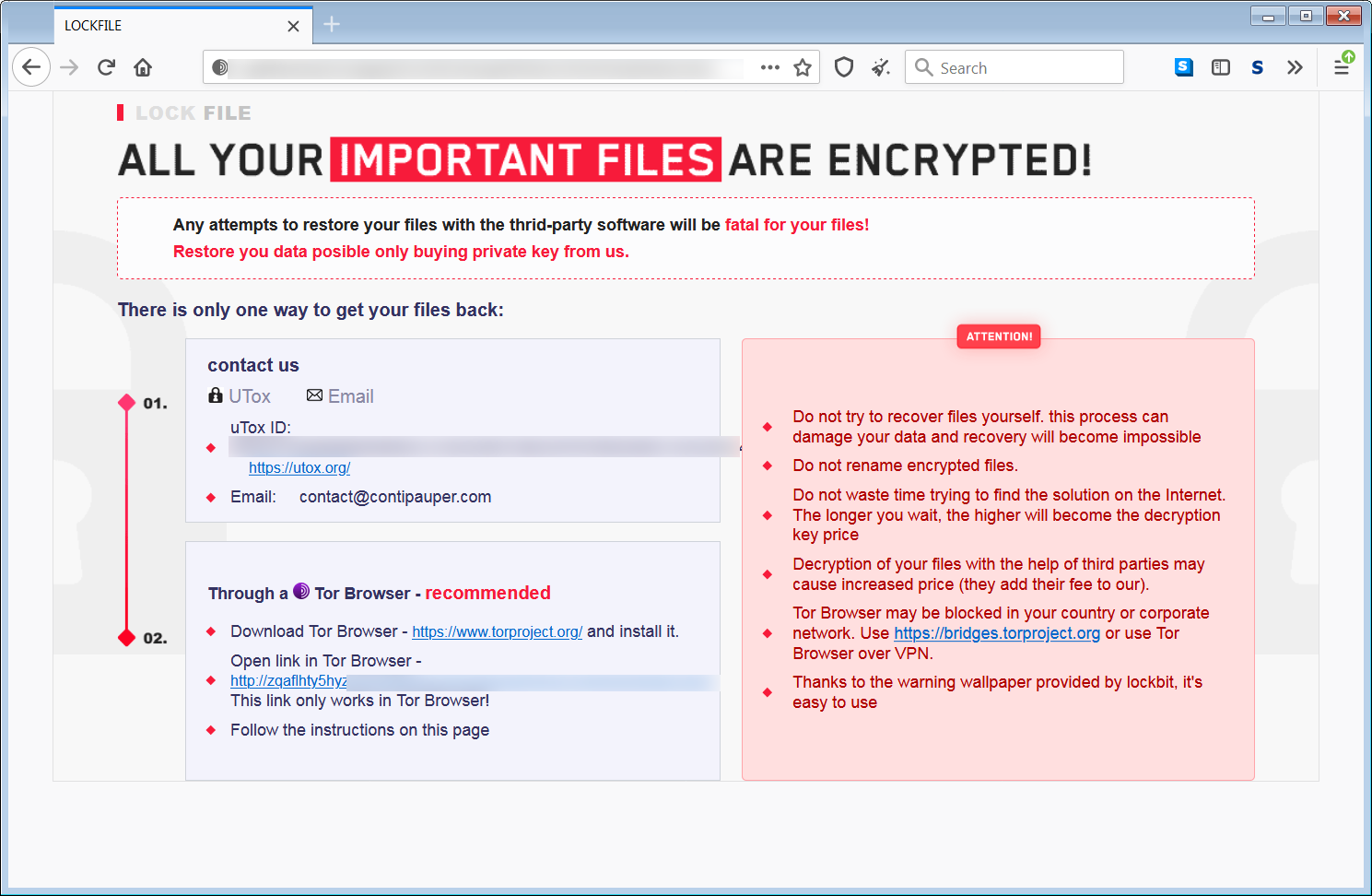
Furthermore, it looks like the new gang also makes a not-so-subtle reference to the Conti gang in the contact email address they leave for the victim: contact@contipauper[.]com.
