In a concerning development, cybercriminals are exploiting trusted Google services—particularly Google Sites and DomainKeys Identified Mail (DKIM)—to bypass traditional security mechanisms and execute highly deceptive phishing campaigns. This evolving tactic allows attackers to deliver legitimate-looking emails that are difficult to detect by even the most sophisticated spam filters.
How the Google Sites Phishing Attack Works
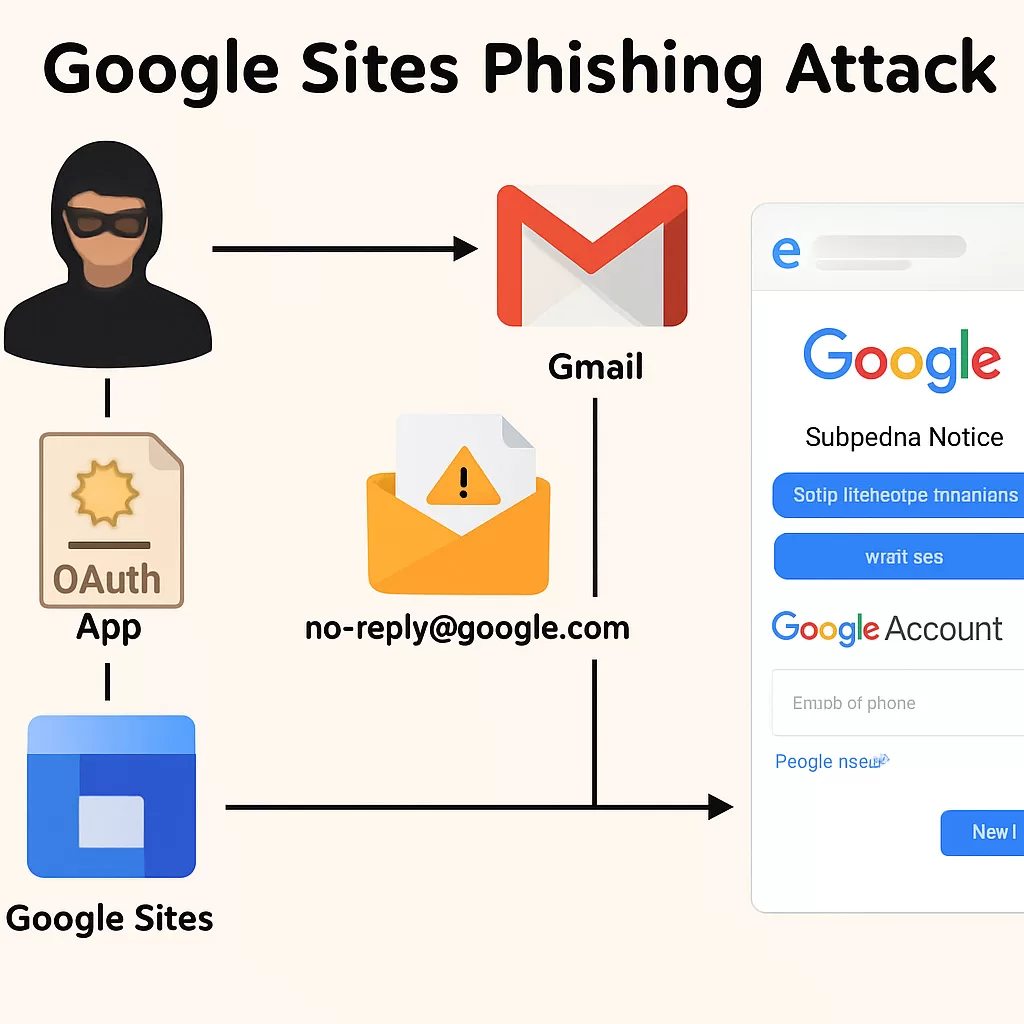
The attack begins with threat actors creating malicious webpages using Google Sites, which inherently benefits from the google.com domain reputation. These pages are cleverly disguised as Google’s official support pages, mimicking the look and feel of legitimate service portals.
Attackers combine this tactic with manipulated DKIM-signed emails—a method that adds another layer of authenticity to their phishing efforts. DKIM is an email authentication method designed to detect forged sender addresses, and emails sent from Google’s servers typically pass DKIM validation.
The phishing emails in this campaign originate from no-reply@google.com, referencing fabricated legal notices or subpoenas involving the recipient’s Google account. These emails are not only signed with valid DKIM signatures, but they also include links pointing to the attacker’s Google Sites phishing pages.
Once recipients click the link, they’re redirected to what appears to be a legitimate Google login page. However, entering their credentials sends sensitive data directly into the hands of cybercriminals.
Abuse of Google OAuth and Security Notifications
Security researchers discovered that the attackers registered OAuth applications through Google Cloud, giving these apps permission to access user accounts. When a user grants access to the app, Google sends out a legitimate security alert email—ironically warning users of a new sign-in or permission request.
By forwarding this authentic Google-generated alert to their targets, attackers ensure the email passes DKIM, SPF, and DMARC checks, making the phishing email appear 100% trustworthy.
Why This Attack Is Dangerous
The campaign exploits the inherent trust in Google’s infrastructure—including the domains, brand, and email systems. Even tech-savvy users may fall victim due to the combination of real-looking Google Sites, authentic email headers, and security alerts actually generated by Google.
This campaign marks a significant evolution in phishing techniques, blending social engineering with technical exploitation of cloud services. The use of legitimate services makes these phishing attempts nearly impossible to detect using conventional email security solutions.
Google’s Response and User Recommendations
Google has acknowledged the campaign and is actively working to shut down malicious pages and block offending OAuth applications. The company reiterated that Google will never ask users to submit sensitive information via email, especially regarding subpoenas or legal notices.
Users are encouraged to:
- Enable 2-step verification or passkeys
- Regularly review account access permissions
- Be cautious of unexpected emails—even if they appear to come from Google
- Avoid clicking on unsolicited links or submitting credentials on unfamiliar pages
Final Thoughts
This Google Sites phishing attack highlights the increasing sophistication of cybercriminal tactics. As trusted platforms like Google are misused, it becomes crucial for users and enterprises to adopt layered security practices, stay informed about emerging threats, and remain skeptical of even the most legitimate-looking emails.