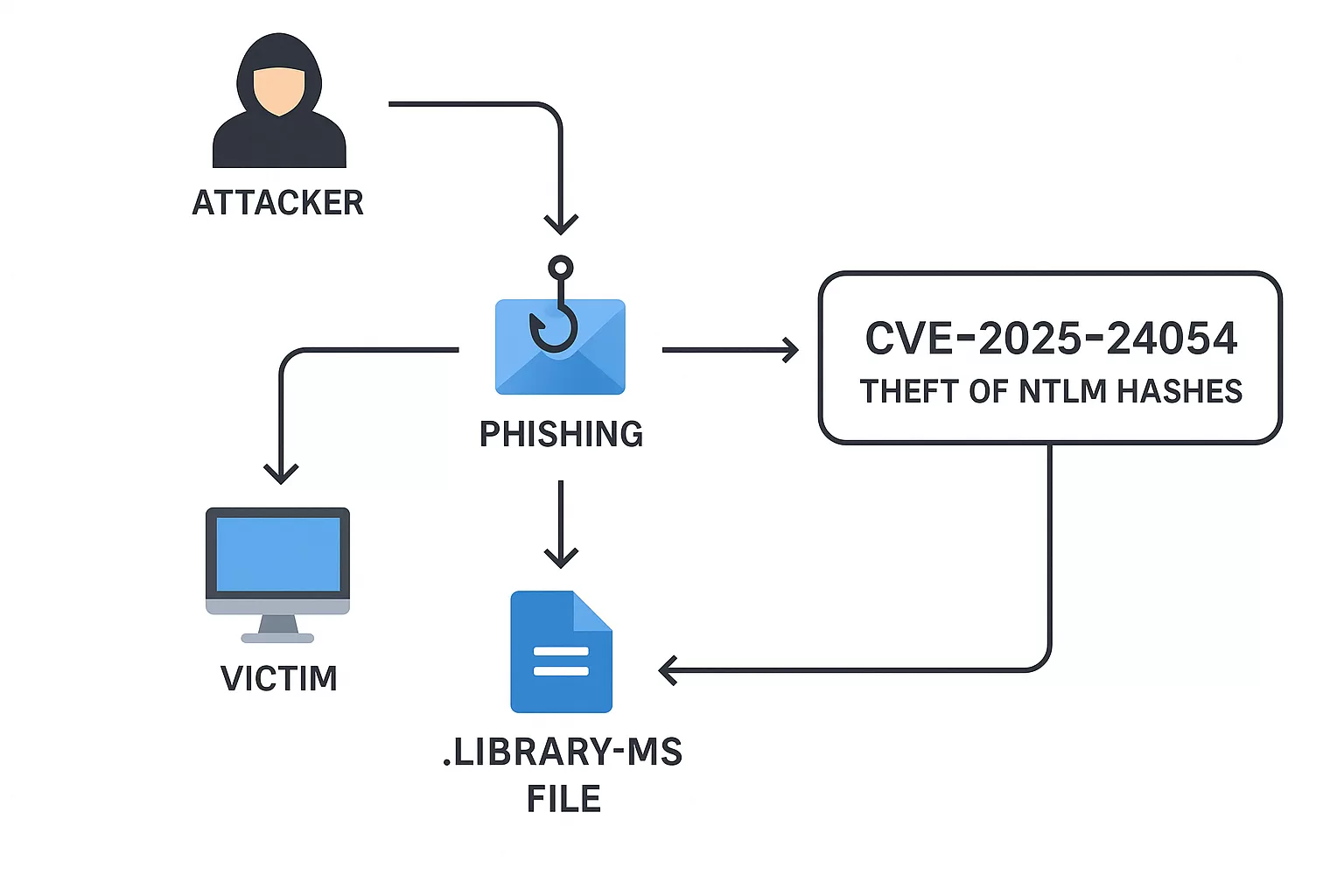
A medium-severity vulnerability in Microsoft Windows, identified as CVE-2025-24054, is currently under active exploitation, enabling attackers to steal NTLM credentials through minimal user interaction. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added this flaw to its Known Exploited Vulnerabilities (KEV) catalog following reports of real-world attacks.
Vulnerability Details
CVE-2025-24054 is a spoofing vulnerability affecting the Windows New Technology LAN Manager (NTLM) authentication protocol. Despite Microsoft’s deprecation of NTLM in favor of Kerberos, NTLM remains in use across various systems. The vulnerability arises from improper handling of file names or paths, allowing unauthorized attackers to perform spoofing over a network.
The issue can be triggered by minimal interaction with a specially crafted .library-ms file, such as selecting or inspecting the file, without the need to open or execute it. This interaction can lead to the unintended disclosure of NTLM hashes, which attackers can use for further exploitation.
Active Exploitation
Security researchers have observed active exploitation of this vulnerability since March 19, 2025. Attackers have employed phishing campaigns distributing malicious .library-ms files via Dropbox links or ZIP archives. In one campaign targeting organizations in Poland and Romania, victims received emails containing archives that, when extracted, triggered the vulnerability to leak NTLMv2-SSP hashes.
Another campaign observed on March 25, 2025, delivered an uncompressed file named “Info.doc.library-ms” to victims. Since the initial wave of attacks, at least ten campaigns have been identified, all aiming to harvest NTLM hashes from targeted individuals.
Implications and Recommendations
The theft of NTLM hashes poses significant security risks, including the potential for pass-the-hash attacks, lateral movement within networks, and privilege escalation. Given the minimal user interaction required to exploit this vulnerability, organizations are urged to take immediate action.
Microsoft released a patch for CVE-2025-24054 in March 2025 as part of its Patch Tuesday updates. Organizations should ensure that all systems are updated with the latest security patches. Additionally, CISA has mandated that Federal Civilian Executive Branch agencies apply the necessary fixes by May 8, 2025, to mitigate the risk of exploitation.
Security teams are advised to audit their environments for the presence of .library-ms files and monitor for unusual SMB authentication requests, which may indicate attempts to exploit this vulnerability.